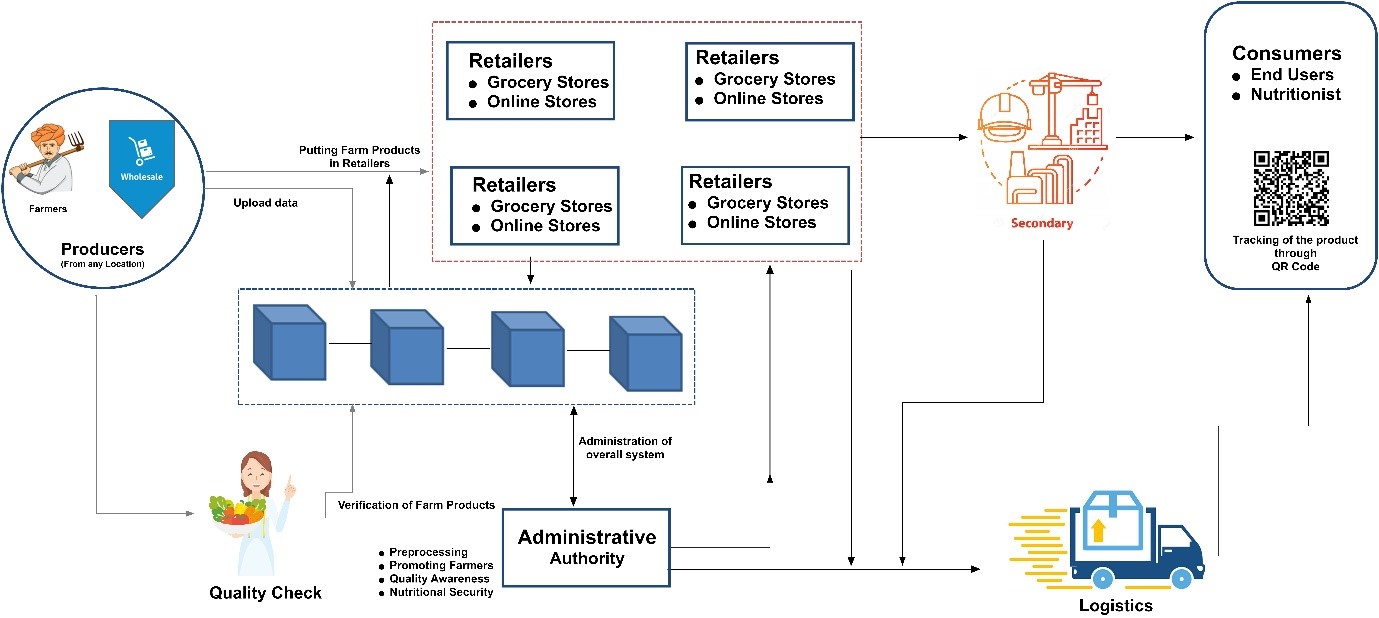
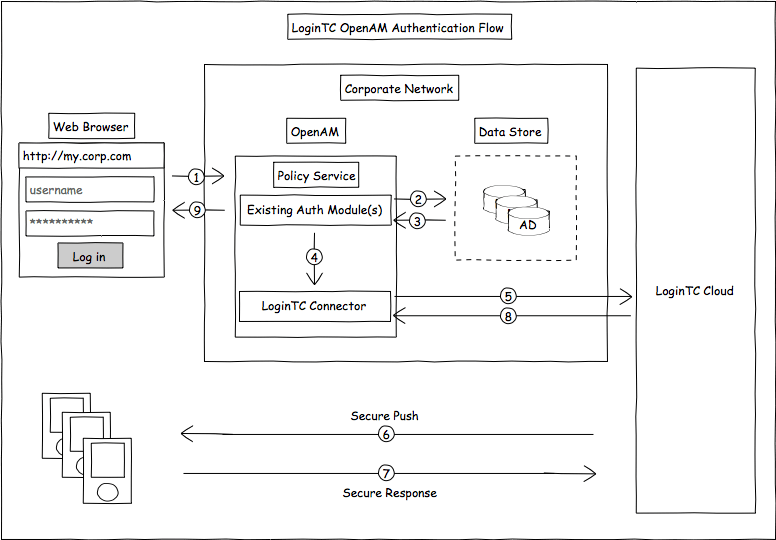
Mobile-Chain: Secure blockchain based decentralized authentication system for global roaming in mobility networks - ScienceDirect
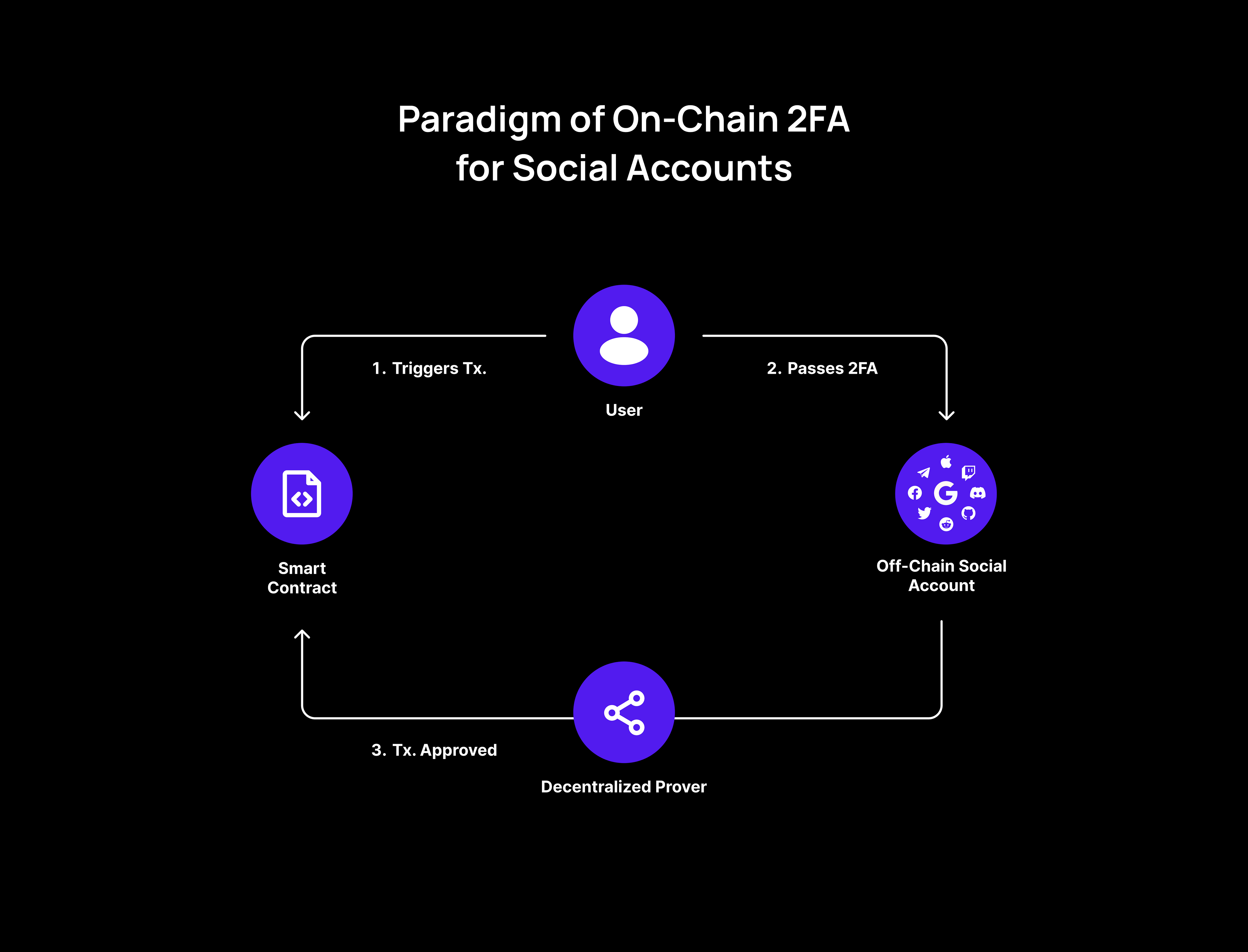
A Proposal of on-chain verifiable Social Identity 2 Factor Authentication - EIPs - Fellowship of Ethereum Magicians
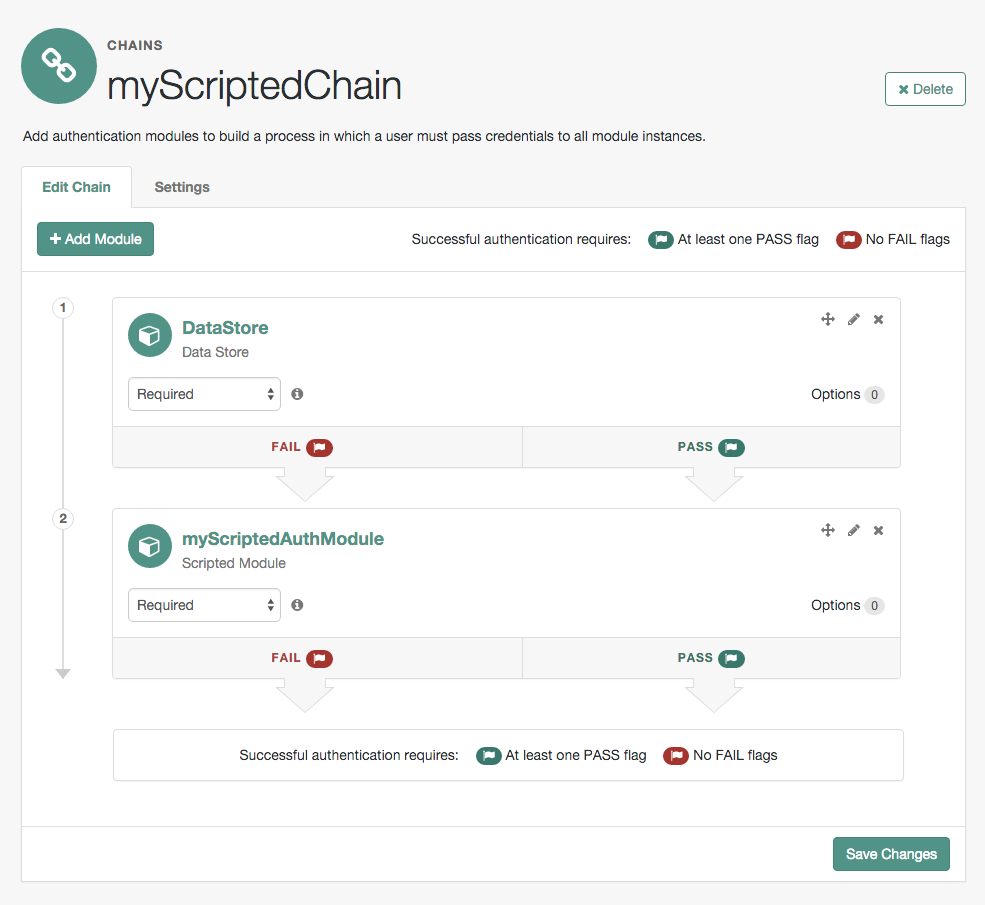
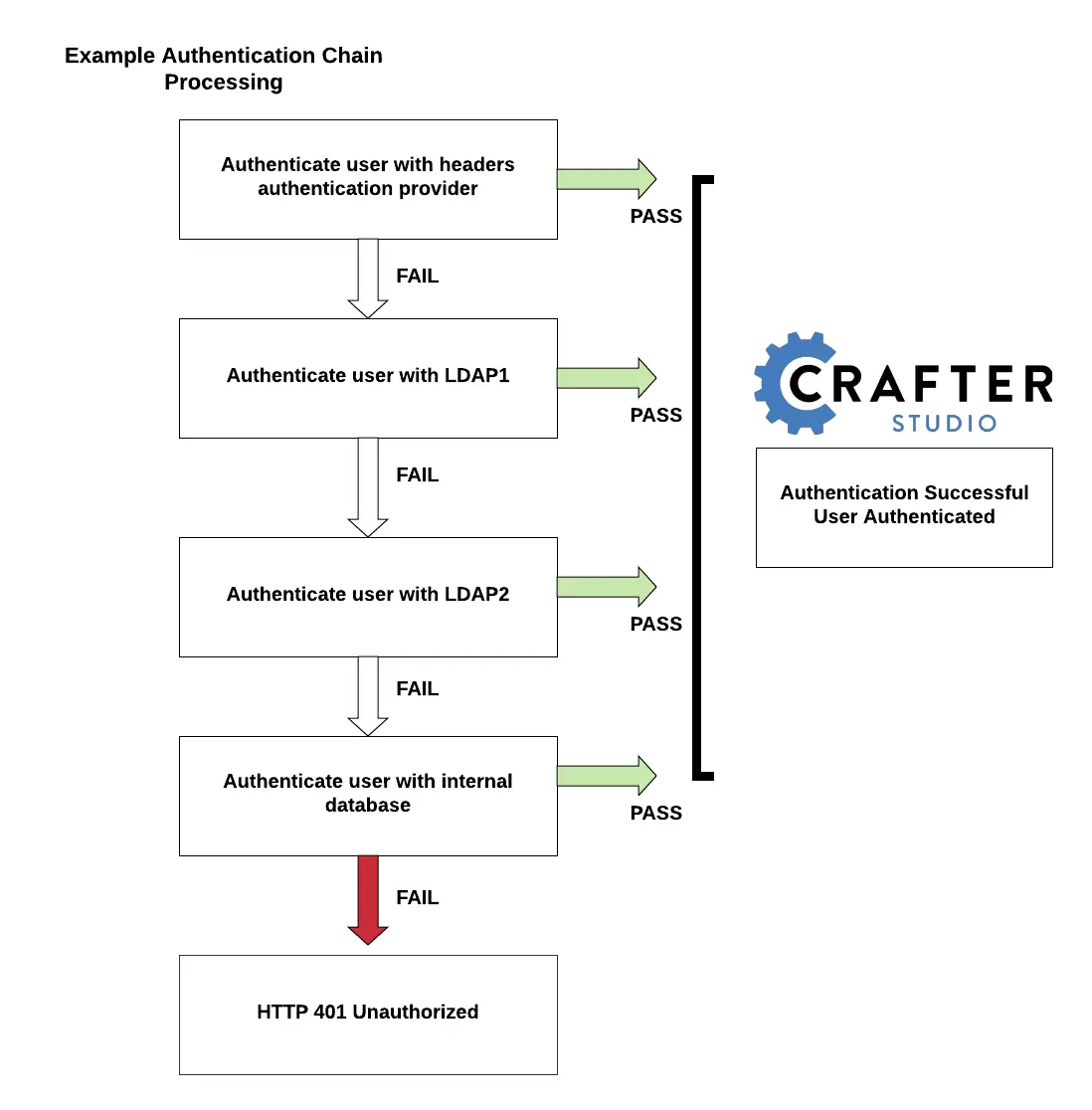
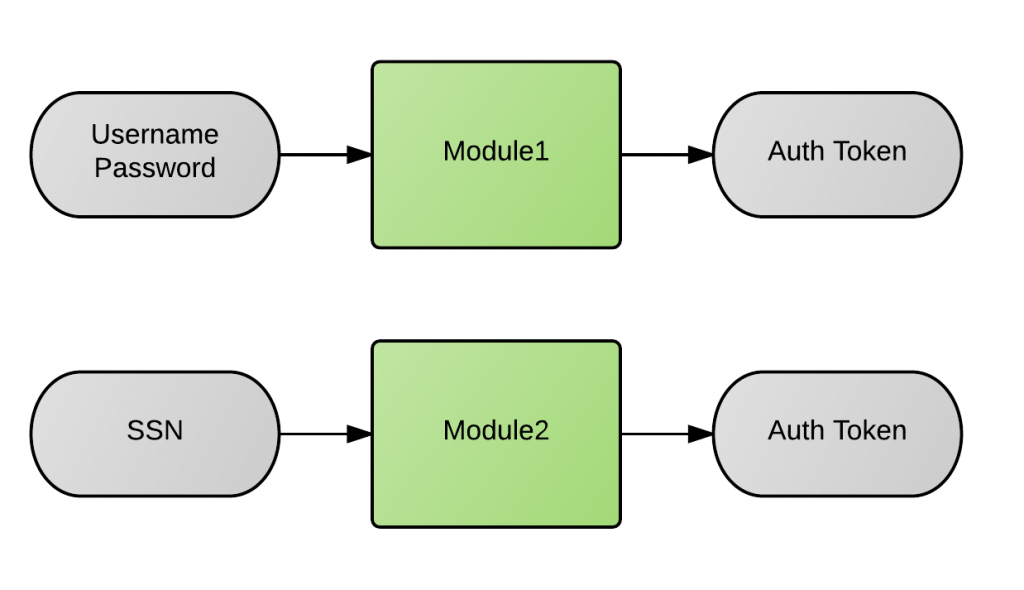
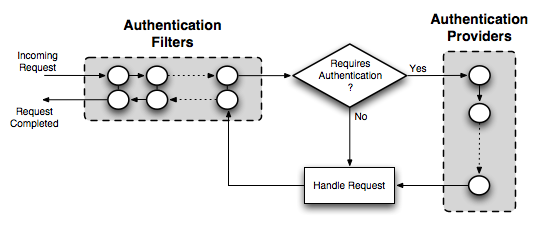
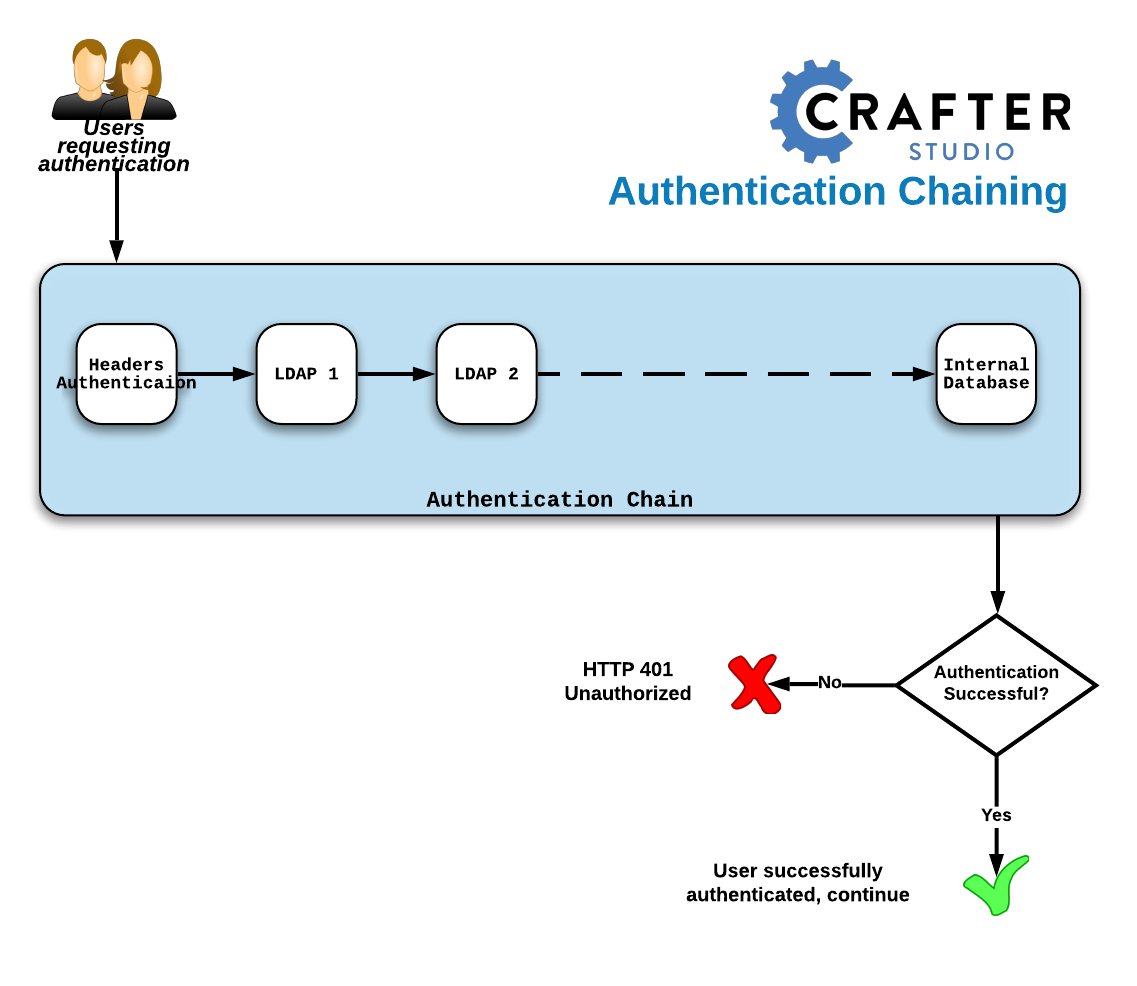
ForgeRock Access Management 7.0.2 > Authentication and Single Sign-On Guide > Authentication Modules and Chains

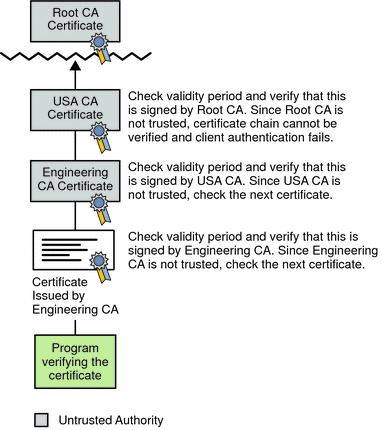
Typical certificate chains; the authorization chain (verified by the... | Download Scientific Diagram

Code Authentication Unit verifies the integrity of the chain of trust,... | Download Scientific Diagram
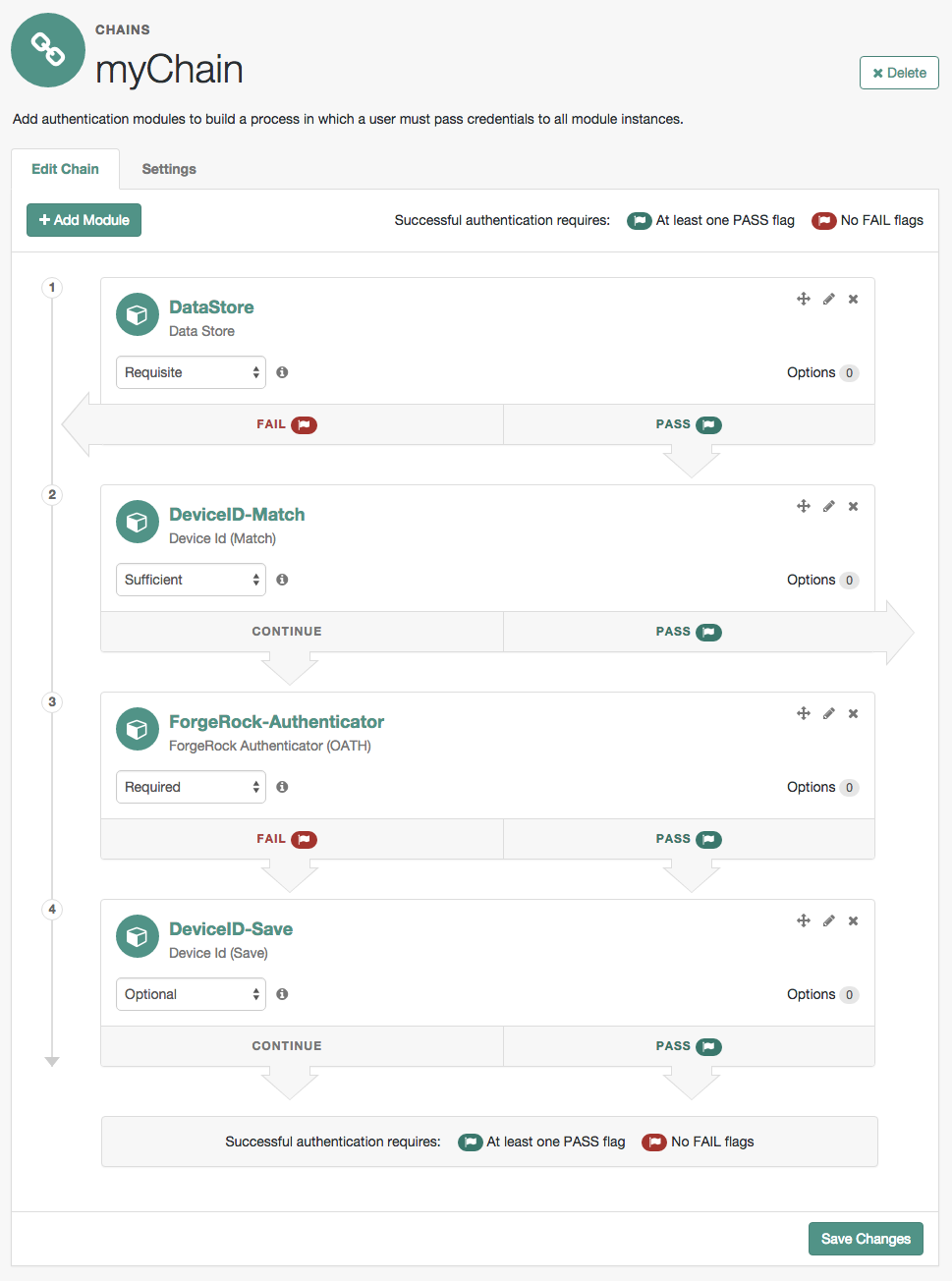
ForgeRock Access Management 7.0.2 > Authentication and Single Sign-On Guide > Authentication Modules and Chains